In everyday security work, especially in threat analysis and phishing investigation, professionals often encounter shortened URLs: bit.ly, tinyurl, t.co, cutt.ly, and hundreds of others. These links are used not only for convenience but also to hide the final destination address.
Why Use a DOLG Unshortener Tool
In practice, shortened URLs cause several problems:
- Opacity — You can’t see where the link leads without opening it.
- Phishing risks — Attackers often use shortened links to bypass filters and trick users.
- No safe audit trail — Browsers follow redirects automatically without showing intermediate steps.
This script was born from a real-world need — to analyze short URLs without opening them in a browser, see all redirect steps, HTTP headers, status codes, and the final destination URL. Originally, I used CLI tools in Ubuntu, but it wasn’t convenient. That’s why I built this tool — a PHP-based solution that can run on any regular hosting.
Goals and Features
The goal was to create a simple and secure tool for:
- Security researchers and threat analysts;
- IT forensics and SOC teams;
- Anyone working with links, marketing, or SMM.
The script is designed to:
- Reveal full redirect chains behind any shortened link;
- Protect your server from SSRF and unsafe requests;
- Display HTTP headers, status codes, and content types;
- Work in any browser via a lightweight HTML/CSS UI;
- Run on any PHP server without dependencies.
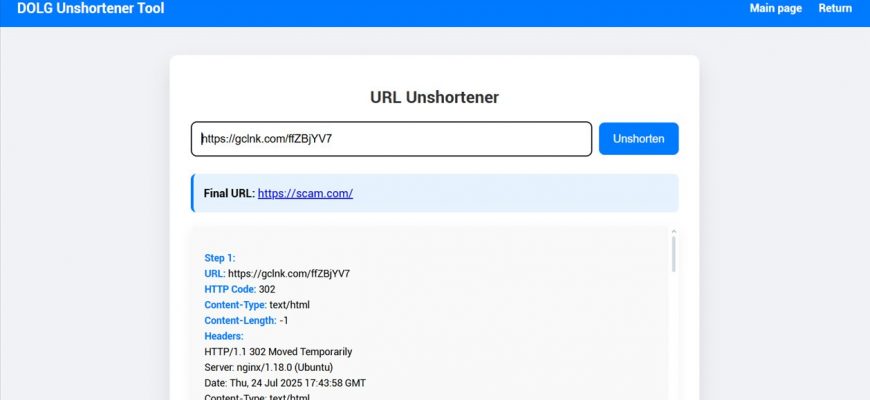
How the Script Works
The user enters a short URL (e.g., bit.ly), and the script sends a raw HTTP request to that address. It manually follows the chain of redirects by checking for the Location header — up to 10 times — and shows the final result.
Redirect Analysis Logic
- Validates the URL;
- Resolves the IP and blocks private/local addresses;
- Initializes a
cURLsession with disabledFOLLOWLOCATION; - Extracts all headers, HTTP code, and
Locationvalues manually; - Stores the results step-by-step in a structured log array;
- Shows the final link in a clickable and safe format.
Use Cases
1. Phishing Email Analysis
Check where a suspicious link really leads, without ever opening it. Perfect for malware analysts and SOC specialists.
2. Affiliate and Advertising URL Audits
Reveal the true final landing page behind masked or cloaked links — ideal for affiliate managers and marketers.
3. Social Media Link Transparency
Services like t.co or lnkd.in obscure URLs. This tool shows what they hide before you click.
4. Digital Forensics
Document full HTTP redirect chains and metadata without risking infection. Useful in forensic reports and court-accepted logs.
Why This Script Is Worth Using
- 100% safe — it blocks internal IPs and SSRF attempts;
- No setup needed — works on any PHP-enabled hosting;
- Fast and efficient — no external dependencies or frameworks;
- Transparent — shows all HTTP-level behavior of a short link.
Conclusion
If you work with shortened URLs and want to analyze them safely and transparently, this script will save you time, reduce risk, and give you full visibility. You can install it on your server and start using it right away.