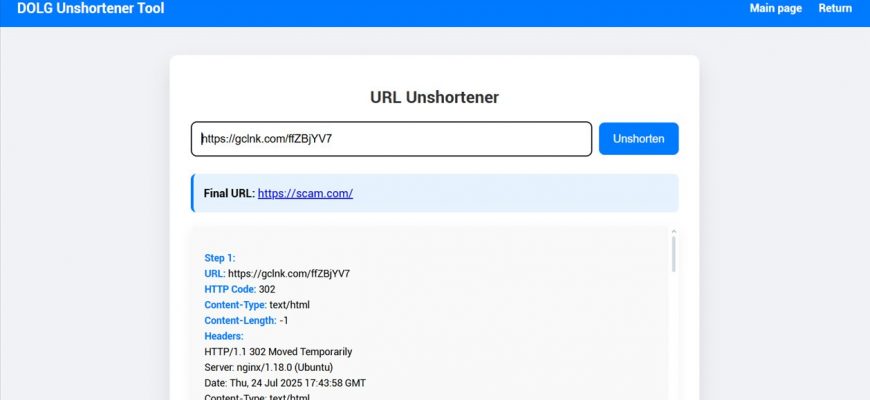
In everyday security work, especially in threat analysis and phishing investigation, professionals often encounter shortened URLs: bit.ly, tinyurl, t.
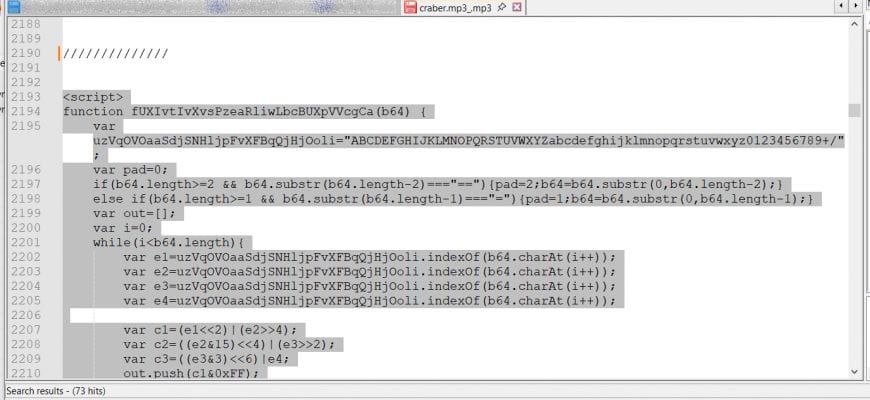
Introduction In this article, we explore an unusual but dangerous method of compromising a Windows workstation. The attack uses social engineering and
Cybersecurity
Today, I want to raise an important issue of information security and discuss short link services that are used within companies and by specific groups of employees.